Key Insights
The Asia-Pacific (APAC) Internet of Things (IoT) security market is experiencing explosive growth, driven by the rapid proliferation of connected devices across diverse sectors. A compound annual growth rate (CAGR) of 38.67% from 2019 to 2024 suggests a significant market expansion. This growth is fueled by increasing government regulations mandating robust cybersecurity measures, particularly in sensitive sectors like healthcare and finance (BFSI). The rising adoption of cloud-based solutions and the expanding network of interconnected devices in smart homes, manufacturing, and supply chain operations are key catalysts. Furthermore, the increasing prevalence of sophisticated cyber threats and data breaches is compelling organizations to invest heavily in robust security solutions. While the market faces challenges such as interoperability issues between different IoT devices and a shortage of skilled cybersecurity professionals, these hurdles are being steadily overcome by technological advancements and increased investment in training. The demand for a broad spectrum of security solutions, including Identity Access Management (IAM), Intrusion Prevention Systems (IPS), and Data Loss Prevention (DLP), is driving market segmentation and specialization. Key players are strategically positioning themselves to capitalize on these trends by offering comprehensive security solutions tailored to the unique needs of various verticals.
The market's robust growth trajectory is expected to continue throughout the forecast period (2025-2033). While precise figures for regional market share within APAC (e.g., China, India, Japan) are not provided, considering the overall CAGR and the significant economic activity and technological adoption in China and India, we can anticipate that these two nations will represent a substantial portion of the overall APAC market. The strong emphasis on digital transformation initiatives across various APAC governments and the burgeoning adoption of IoT in smart city infrastructure will further fuel the market's expansion. Significant opportunities exist for companies offering advanced security solutions that address emerging threats related to artificial intelligence (AI)-powered attacks and the increasing reliance on edge computing. This growth will also be shaped by factors like the maturation of IoT standards and the development of more user-friendly and cost-effective security solutions.
This comprehensive report provides a detailed analysis of the Asia-Pacific (APAC) Internet of Things (IoT) security market, offering invaluable insights for industry professionals, investors, and strategists. The study period covers 2019-2033, with a base year of 2025 and a forecast period of 2025-2033. The report leverages extensive data and analysis to provide a clear understanding of market dynamics, growth drivers, challenges, and future opportunities within this rapidly evolving sector. The market is valued at xx Million in 2025 and is projected to reach xx Million by 2033, exhibiting a CAGR of xx%.
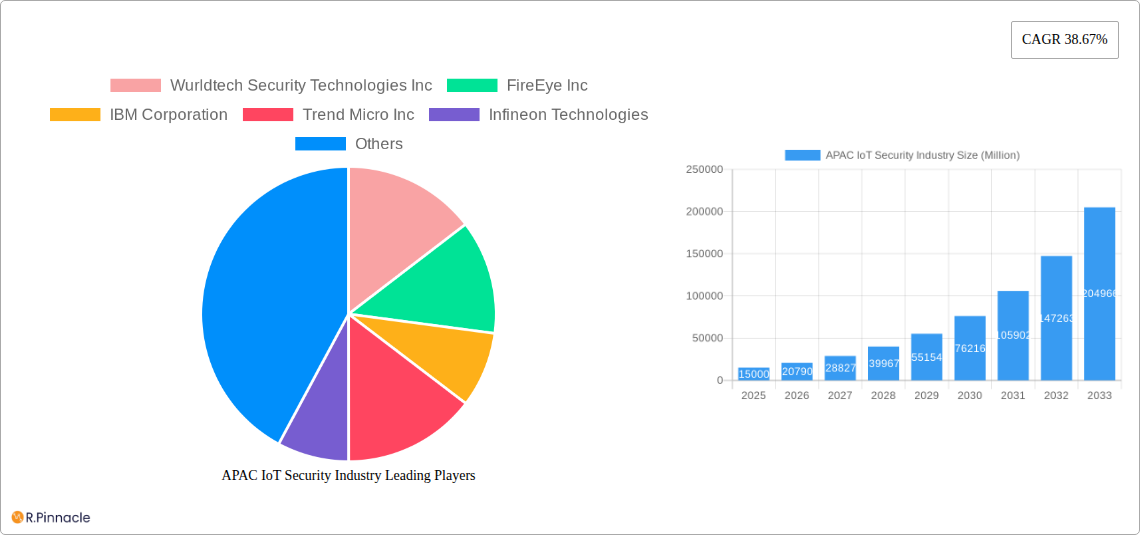
APAC IoT Security Industry Market Structure & Innovation Trends
The APAC IoT security market exhibits a moderately concentrated structure, with several major players holding significant market share. Key players include IBM Corporation, Trend Micro Inc, Intel Corporation, Sophos Group PLC, ARM Holdings PLC, Symantec Corporation (NortonLifeLock Inc), Infineon Technologies, Gemalto NV, FireEye Inc, and Wurldtech Security Technologies Inc. However, the market also accommodates numerous smaller, specialized firms. Market share distribution among these companies varies significantly depending on the segment (e.g., network security vs. endpoint security). The total M&A activity value in the APAC IoT security market between 2019-2024 is estimated at xx Million, reflecting significant consolidation and investment in the sector.
- Innovation Drivers: Increasing IoT adoption across various sectors (healthcare, manufacturing, BFSI), growing awareness of cybersecurity threats, and evolving regulatory compliance requirements are major drivers of innovation.
- Regulatory Frameworks: Differing data privacy regulations across APAC nations influence product development and market strategies.
- Product Substitutes: The absence of readily available, fully effective substitutes for specialized IoT security solutions reinforces market growth.
- End-User Demographics: The market is driven by a diverse range of end-users, including large enterprises, SMEs, and government agencies, each with specific security needs.
- M&A Activities: Strategic acquisitions and mergers facilitate market expansion, technological integration, and increased market share for leading players.
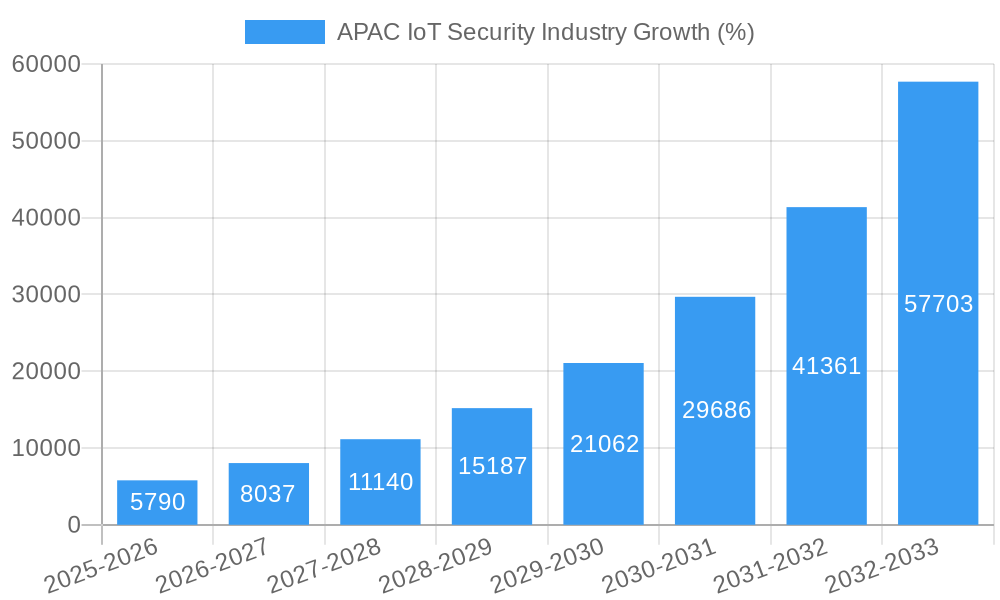
APAC IoT Security Industry Market Dynamics & Trends
The APAC IoT security market is characterized by robust growth, fueled by several key factors. The increasing adoption of IoT devices across various sectors, coupled with rising cyber threats, drives demand for robust security solutions. Technological advancements, including AI-powered security analytics and edge computing, further enhance market growth. Consumer preferences are shifting towards integrated and user-friendly security solutions. Competitive dynamics are intense, with established players and emerging startups vying for market share through product innovation, strategic partnerships, and mergers and acquisitions. The market is expected to experience a xx% CAGR between 2025 and 2033, with significant market penetration across all major segments.

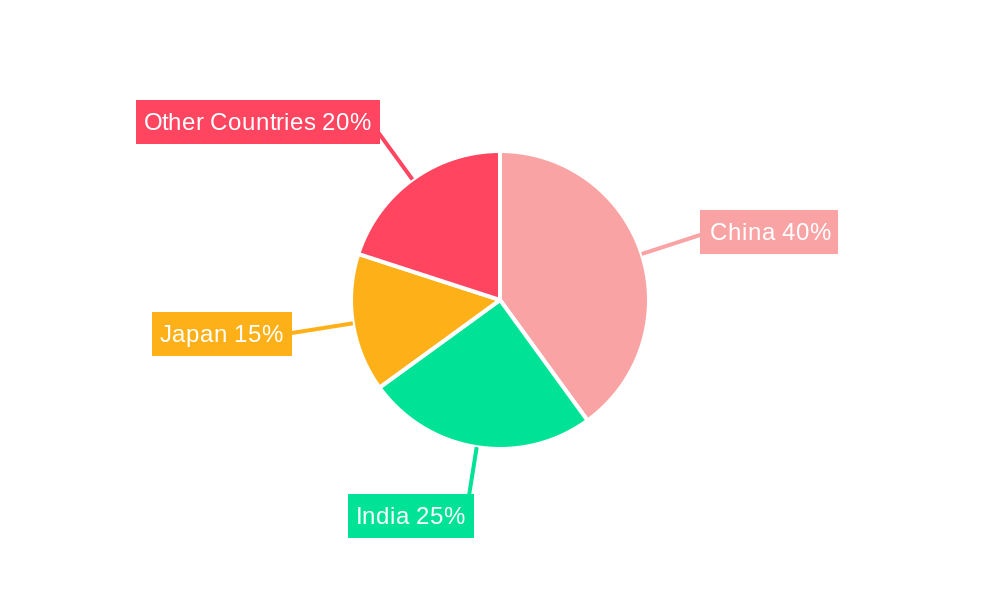
Dominant Regions & Segments in APAC IoT Security Industry
The APAC IoT security market shows significant regional variations in growth rates and segment dominance. While specific data on precise market share for each segment within each region would require extensive investigation beyond the scope provided, we can make some generalized observations based on industry trends. China, India, Japan, South Korea, and Australia are among the leading markets due to high IoT adoption, robust economic growth, and significant government investments.
Key Drivers:
- Economic Policies: Government initiatives promoting digital transformation and investment in infrastructure drive IoT adoption, creating greater demand for security solutions.
- Infrastructure Development: Expansion of 5G networks and cloud computing capabilities facilitates broader IoT deployment and increases reliance on security solutions.
Dominant Segments (Illustrative examples based on general trends):
- Type of Security: Network security and endpoint security are currently dominant segments, with cloud security rapidly gaining traction.
- Solutions: Identity Access Management (IAM), Intrusion Prevention Systems (IPS), and Data Loss Prevention (DLP) solutions are widely adopted.
- Applications: Manufacturing Process Management, Supply Chain Operation, and Patient Information Management (within healthcare) demonstrate significant demand.
- End-User Verticals: Manufacturing, Healthcare, and BFSI (Banking, Financial Services, and Insurance) sectors are major end-users due to the critical nature of their data.
APAC IoT Security Industry Product Innovations
Recent product innovations focus on AI-powered threat detection, advanced encryption techniques, and simplified management interfaces. The market is seeing a shift towards cloud-based security solutions and integrated security platforms that offer comprehensive protection across various IoT devices and applications. This trend aligns with the growing need for seamless security management across complex IoT ecosystems and reflects a market preference for solutions that can reduce the burden on IT teams, while simultaneously bolstering protection against increasingly sophisticated cyber threats.
Report Scope & Segmentation Analysis
This report segments the APAC IoT security market based on:
Type of Security: Network Security, Endpoint Security, Application Security, Cloud Security, Other types of security. Each segment's market size, growth projections, and competitive landscape are analyzed individually, reflecting variations in technology adoption rates and deployment models.
Solutions: Identity Access Management (IAM), Intrusion Prevention System (IPS), Data Loss Protection (DLP), Unified Threat Management (UTM), Security & Vulnerability Management (SVM), Network Security Forensics (NSF), Other solutions. The report examines the specific market demand for each security solution category, accounting for evolving threats and organizational security priorities.
Applications: Home Automation, Wearables, Manufacturing Process Management, Patient Information Management, Supply Chain Operation, Customer Information Security, Other applications. The unique security requirements of each application segment are carefully considered, providing insight into specialized solution adoption rates.
End-User Verticals: Healthcare, Manufacturing, Utilities, BFSI, Retail, Government, Other end-user verticals. Each sector’s distinctive security challenges and investment priorities are assessed.
Key Drivers of APAC IoT Security Industry Growth
The growth of the APAC IoT security market is driven by several key factors: the increasing number of connected devices, rising cybersecurity threats, stringent government regulations concerning data privacy and security, substantial investments in infrastructure, and the expanding adoption of cloud computing and edge computing technologies. Furthermore, economic development across APAC is contributing to the growth by fueling greater investment in technological advancements that create new IoT applications and demand for robust security solutions.
Challenges in the APAC IoT Security Industry Sector
Key challenges include the diverse regulatory landscape across APAC countries, the complexity of securing heterogeneous IoT environments, skills gaps in cybersecurity expertise, and the rising sophistication of cyberattacks. Supply chain vulnerabilities also pose significant threats, with the potential for compromised devices to introduce security breaches into the broader IoT ecosystem. These factors lead to increased costs for businesses and create difficulties for effective security implementation.
Emerging Opportunities in APAC IoT Security Industry
Significant opportunities exist in developing specialized security solutions for emerging IoT applications (e.g., smart cities, autonomous vehicles), leveraging AI and machine learning for proactive threat detection, and fostering greater collaboration between stakeholders (governments, industry, researchers) to improve security standards and share best practices. Expanding the adoption of secure design principles from the outset of IoT device development also represents a critical opportunity to strengthen overall ecosystem security.
Leading Players in the APAC IoT Security Industry Market
- Wurldtech Security Technologies Inc
- FireEye Inc
- IBM Corporation
- Trend Micro Inc
- Infineon Technologies
- Gemalto NV
- Symantec Corporation (NortonLifeLock Inc)
- ARM Holdings PLC
- Sophos Group PLC
- Intel Corporation
Key Developments in APAC IoT Security Industry Industry
- August 2022: Truvisor partnered with One Identity to deliver identity security solutions across Singapore, the Philippines, and Indonesia, expanding market reach.
- April 2022: Swimlane launched Swimlane Cloud in APJ, offering low-code security automation to enhance response times and compliance.
Future Outlook for APAC IoT Security Market
The APAC IoT security market is poised for substantial growth, driven by increasing IoT adoption, escalating cybersecurity concerns, and evolving regulatory requirements. Strategic partnerships, technological innovation, and investments in cybersecurity expertise will play crucial roles in shaping the future landscape. The market's success hinges on the ability of vendors to provide comprehensive, user-friendly, and cost-effective security solutions that address the unique challenges of securing diverse IoT environments.
APAC IoT Security Industry Segmentation
-
1. Type of Security
- 1.1. Network Security
- 1.2. Endpoint Security
- 1.3. Application Security
- 1.4. Cloud Security
- 1.5. Other types of security
-
2. Solutions
- 2.1. Identity Access Management (IAM)
- 2.2. Intrusion Prevention System (IPS)
- 2.3. Data Loss Protection (DLP)
- 2.4. Unified Threat Management (UTM)
- 2.5. Security & Vulnerability Management (SVM)
- 2.6. Network Security Forensics (NSF)
- 2.7. Other solutions
-
3. Applications
- 3.1. Home Automation
- 3.2. Wearables
- 3.3. Manufacturing Process Management
- 3.4. Patient Information Management
- 3.5. Supply Chain Operation
- 3.6. Customer Information Security
- 3.7. Other applications
-
4. End-User Verticals
- 4.1. Healthcare
- 4.2. Manufacturing
- 4.3. Utilities
- 4.4. BFSI
- 4.5. Retail
- 4.6. Government
- 4.7. Other end-user verticals
-
5. Geography
- 5.1. China
- 5.2. India
- 5.3. Japan
- 5.4. Other countries
APAC IoT Security Industry Segmentation By Geography
- 1. China
- 2. India
- 3. Japan
- 4. Other countries
APAC IoT Security Industry REPORT HIGHLIGHTS
| Aspects | Details |
|---|---|
| Study Period | 2019-2033 |
| Base Year | 2024 |
| Estimated Year | 2025 |
| Forecast Period | 2025-2033 |
| Historical Period | 2019-2024 |
| Growth Rate | CAGR of 38.67% from 2019-2033 |
| Segmentation |
|
Table of Contents
- 1. Introduction
- 1.1. Research Scope
- 1.2. Market Segmentation
- 1.3. Research Methodology
- 1.4. Definitions and Assumptions
- 2. Executive Summary
- 2.1. Introduction
- 3. Market Dynamics
- 3.1. Introduction
- 3.2. Market Drivers
- 3.2.1. Increasing Number of Data Breaches; Emergence of Smart Cities
- 3.3. Market Restrains
- 3.3.1 Growing Complexity among Devices
- 3.3.2 coupled with the Lack of Ubiquitous Legislation
- 3.4. Market Trends
- 3.4.1. Emergence of Smart City and Smart Home Developments to Drive the Market Growth
- 4. Market Factor Analysis
- 4.1. Porters Five Forces
- 4.2. Supply/Value Chain
- 4.3. PESTEL analysis
- 4.4. Market Entropy
- 4.5. Patent/Trademark Analysis
- 5. APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 5.1. Market Analysis, Insights and Forecast - by Type of Security
- 5.1.1. Network Security
- 5.1.2. Endpoint Security
- 5.1.3. Application Security
- 5.1.4. Cloud Security
- 5.1.5. Other types of security
- 5.2. Market Analysis, Insights and Forecast - by Solutions
- 5.2.1. Identity Access Management (IAM)
- 5.2.2. Intrusion Prevention System (IPS)
- 5.2.3. Data Loss Protection (DLP)
- 5.2.4. Unified Threat Management (UTM)
- 5.2.5. Security & Vulnerability Management (SVM)
- 5.2.6. Network Security Forensics (NSF)
- 5.2.7. Other solutions
- 5.3. Market Analysis, Insights and Forecast - by Applications
- 5.3.1. Home Automation
- 5.3.2. Wearables
- 5.3.3. Manufacturing Process Management
- 5.3.4. Patient Information Management
- 5.3.5. Supply Chain Operation
- 5.3.6. Customer Information Security
- 5.3.7. Other applications
- 5.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 5.4.1. Healthcare
- 5.4.2. Manufacturing
- 5.4.3. Utilities
- 5.4.4. BFSI
- 5.4.5. Retail
- 5.4.6. Government
- 5.4.7. Other end-user verticals
- 5.5. Market Analysis, Insights and Forecast - by Geography
- 5.5.1. China
- 5.5.2. India
- 5.5.3. Japan
- 5.5.4. Other countries
- 5.6. Market Analysis, Insights and Forecast - by Region
- 5.6.1. China
- 5.6.2. India
- 5.6.3. Japan
- 5.6.4. Other countries
- 5.1. Market Analysis, Insights and Forecast - by Type of Security
- 6. China APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 6.1. Market Analysis, Insights and Forecast - by Type of Security
- 6.1.1. Network Security
- 6.1.2. Endpoint Security
- 6.1.3. Application Security
- 6.1.4. Cloud Security
- 6.1.5. Other types of security
- 6.2. Market Analysis, Insights and Forecast - by Solutions
- 6.2.1. Identity Access Management (IAM)
- 6.2.2. Intrusion Prevention System (IPS)
- 6.2.3. Data Loss Protection (DLP)
- 6.2.4. Unified Threat Management (UTM)
- 6.2.5. Security & Vulnerability Management (SVM)
- 6.2.6. Network Security Forensics (NSF)
- 6.2.7. Other solutions
- 6.3. Market Analysis, Insights and Forecast - by Applications
- 6.3.1. Home Automation
- 6.3.2. Wearables
- 6.3.3. Manufacturing Process Management
- 6.3.4. Patient Information Management
- 6.3.5. Supply Chain Operation
- 6.3.6. Customer Information Security
- 6.3.7. Other applications
- 6.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 6.4.1. Healthcare
- 6.4.2. Manufacturing
- 6.4.3. Utilities
- 6.4.4. BFSI
- 6.4.5. Retail
- 6.4.6. Government
- 6.4.7. Other end-user verticals
- 6.5. Market Analysis, Insights and Forecast - by Geography
- 6.5.1. China
- 6.5.2. India
- 6.5.3. Japan
- 6.5.4. Other countries
- 6.1. Market Analysis, Insights and Forecast - by Type of Security
- 7. India APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 7.1. Market Analysis, Insights and Forecast - by Type of Security
- 7.1.1. Network Security
- 7.1.2. Endpoint Security
- 7.1.3. Application Security
- 7.1.4. Cloud Security
- 7.1.5. Other types of security
- 7.2. Market Analysis, Insights and Forecast - by Solutions
- 7.2.1. Identity Access Management (IAM)
- 7.2.2. Intrusion Prevention System (IPS)
- 7.2.3. Data Loss Protection (DLP)
- 7.2.4. Unified Threat Management (UTM)
- 7.2.5. Security & Vulnerability Management (SVM)
- 7.2.6. Network Security Forensics (NSF)
- 7.2.7. Other solutions
- 7.3. Market Analysis, Insights and Forecast - by Applications
- 7.3.1. Home Automation
- 7.3.2. Wearables
- 7.3.3. Manufacturing Process Management
- 7.3.4. Patient Information Management
- 7.3.5. Supply Chain Operation
- 7.3.6. Customer Information Security
- 7.3.7. Other applications
- 7.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 7.4.1. Healthcare
- 7.4.2. Manufacturing
- 7.4.3. Utilities
- 7.4.4. BFSI
- 7.4.5. Retail
- 7.4.6. Government
- 7.4.7. Other end-user verticals
- 7.5. Market Analysis, Insights and Forecast - by Geography
- 7.5.1. China
- 7.5.2. India
- 7.5.3. Japan
- 7.5.4. Other countries
- 7.1. Market Analysis, Insights and Forecast - by Type of Security
- 8. Japan APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 8.1. Market Analysis, Insights and Forecast - by Type of Security
- 8.1.1. Network Security
- 8.1.2. Endpoint Security
- 8.1.3. Application Security
- 8.1.4. Cloud Security
- 8.1.5. Other types of security
- 8.2. Market Analysis, Insights and Forecast - by Solutions
- 8.2.1. Identity Access Management (IAM)
- 8.2.2. Intrusion Prevention System (IPS)
- 8.2.3. Data Loss Protection (DLP)
- 8.2.4. Unified Threat Management (UTM)
- 8.2.5. Security & Vulnerability Management (SVM)
- 8.2.6. Network Security Forensics (NSF)
- 8.2.7. Other solutions
- 8.3. Market Analysis, Insights and Forecast - by Applications
- 8.3.1. Home Automation
- 8.3.2. Wearables
- 8.3.3. Manufacturing Process Management
- 8.3.4. Patient Information Management
- 8.3.5. Supply Chain Operation
- 8.3.6. Customer Information Security
- 8.3.7. Other applications
- 8.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 8.4.1. Healthcare
- 8.4.2. Manufacturing
- 8.4.3. Utilities
- 8.4.4. BFSI
- 8.4.5. Retail
- 8.4.6. Government
- 8.4.7. Other end-user verticals
- 8.5. Market Analysis, Insights and Forecast - by Geography
- 8.5.1. China
- 8.5.2. India
- 8.5.3. Japan
- 8.5.4. Other countries
- 8.1. Market Analysis, Insights and Forecast - by Type of Security
- 9. Other countries APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 9.1. Market Analysis, Insights and Forecast - by Type of Security
- 9.1.1. Network Security
- 9.1.2. Endpoint Security
- 9.1.3. Application Security
- 9.1.4. Cloud Security
- 9.1.5. Other types of security
- 9.2. Market Analysis, Insights and Forecast - by Solutions
- 9.2.1. Identity Access Management (IAM)
- 9.2.2. Intrusion Prevention System (IPS)
- 9.2.3. Data Loss Protection (DLP)
- 9.2.4. Unified Threat Management (UTM)
- 9.2.5. Security & Vulnerability Management (SVM)
- 9.2.6. Network Security Forensics (NSF)
- 9.2.7. Other solutions
- 9.3. Market Analysis, Insights and Forecast - by Applications
- 9.3.1. Home Automation
- 9.3.2. Wearables
- 9.3.3. Manufacturing Process Management
- 9.3.4. Patient Information Management
- 9.3.5. Supply Chain Operation
- 9.3.6. Customer Information Security
- 9.3.7. Other applications
- 9.4. Market Analysis, Insights and Forecast - by End-User Verticals
- 9.4.1. Healthcare
- 9.4.2. Manufacturing
- 9.4.3. Utilities
- 9.4.4. BFSI
- 9.4.5. Retail
- 9.4.6. Government
- 9.4.7. Other end-user verticals
- 9.5. Market Analysis, Insights and Forecast - by Geography
- 9.5.1. China
- 9.5.2. India
- 9.5.3. Japan
- 9.5.4. Other countries
- 9.1. Market Analysis, Insights and Forecast - by Type of Security
- 10. China APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 10.1. Market Analysis, Insights and Forecast - By Country/Sub-region
- 10.1.1.
- 11. India APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 11.1. Market Analysis, Insights and Forecast - By Country/Sub-region
- 11.1.1.
- 12. Japan APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 12.1. Market Analysis, Insights and Forecast - By Country/Sub-region
- 12.1.1.
- 13. Other countries APAC IoT Security Industry Analysis, Insights and Forecast, 2019-2031
- 13.1. Market Analysis, Insights and Forecast - By Country/Sub-region
- 13.1.1.
- 14. Competitive Analysis
- 14.1. Market Share Analysis 2024
- 14.2. Company Profiles
- 14.2.1 Wurldtech Security Technologies Inc
- 14.2.1.1. Overview
- 14.2.1.2. Products
- 14.2.1.3. SWOT Analysis
- 14.2.1.4. Recent Developments
- 14.2.1.5. Financials (Based on Availability)
- 14.2.2 FireEye Inc
- 14.2.2.1. Overview
- 14.2.2.2. Products
- 14.2.2.3. SWOT Analysis
- 14.2.2.4. Recent Developments
- 14.2.2.5. Financials (Based on Availability)
- 14.2.3 IBM Corporation
- 14.2.3.1. Overview
- 14.2.3.2. Products
- 14.2.3.3. SWOT Analysis
- 14.2.3.4. Recent Developments
- 14.2.3.5. Financials (Based on Availability)
- 14.2.4 Trend Micro Inc
- 14.2.4.1. Overview
- 14.2.4.2. Products
- 14.2.4.3. SWOT Analysis
- 14.2.4.4. Recent Developments
- 14.2.4.5. Financials (Based on Availability)
- 14.2.5 Infineon Technologies
- 14.2.5.1. Overview
- 14.2.5.2. Products
- 14.2.5.3. SWOT Analysis
- 14.2.5.4. Recent Developments
- 14.2.5.5. Financials (Based on Availability)
- 14.2.6 Gemalto NV*List Not Exhaustive
- 14.2.6.1. Overview
- 14.2.6.2. Products
- 14.2.6.3. SWOT Analysis
- 14.2.6.4. Recent Developments
- 14.2.6.5. Financials (Based on Availability)
- 14.2.7 Symantec Corporation (NortonLifeLock Inc)
- 14.2.7.1. Overview
- 14.2.7.2. Products
- 14.2.7.3. SWOT Analysis
- 14.2.7.4. Recent Developments
- 14.2.7.5. Financials (Based on Availability)
- 14.2.8 ARM Holdings PLC
- 14.2.8.1. Overview
- 14.2.8.2. Products
- 14.2.8.3. SWOT Analysis
- 14.2.8.4. Recent Developments
- 14.2.8.5. Financials (Based on Availability)
- 14.2.9 Sophos Group PLC
- 14.2.9.1. Overview
- 14.2.9.2. Products
- 14.2.9.3. SWOT Analysis
- 14.2.9.4. Recent Developments
- 14.2.9.5. Financials (Based on Availability)
- 14.2.10 Intel Corporation
- 14.2.10.1. Overview
- 14.2.10.2. Products
- 14.2.10.3. SWOT Analysis
- 14.2.10.4. Recent Developments
- 14.2.10.5. Financials (Based on Availability)
- 14.2.1 Wurldtech Security Technologies Inc
List of Figures
- Figure 1: APAC IoT Security Industry Revenue Breakdown (Million, %) by Product 2024 & 2032
- Figure 2: APAC IoT Security Industry Share (%) by Company 2024
List of Tables
- Table 1: APAC IoT Security Industry Revenue Million Forecast, by Region 2019 & 2032
- Table 2: APAC IoT Security Industry Revenue Million Forecast, by Type of Security 2019 & 2032
- Table 3: APAC IoT Security Industry Revenue Million Forecast, by Solutions 2019 & 2032
- Table 4: APAC IoT Security Industry Revenue Million Forecast, by Applications 2019 & 2032
- Table 5: APAC IoT Security Industry Revenue Million Forecast, by End-User Verticals 2019 & 2032
- Table 6: APAC IoT Security Industry Revenue Million Forecast, by Geography 2019 & 2032
- Table 7: APAC IoT Security Industry Revenue Million Forecast, by Region 2019 & 2032
- Table 8: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 9: APAC IoT Security Industry Revenue (Million) Forecast, by Application 2019 & 2032
- Table 10: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 11: APAC IoT Security Industry Revenue (Million) Forecast, by Application 2019 & 2032
- Table 12: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 13: APAC IoT Security Industry Revenue (Million) Forecast, by Application 2019 & 2032
- Table 14: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 15: APAC IoT Security Industry Revenue (Million) Forecast, by Application 2019 & 2032
- Table 16: APAC IoT Security Industry Revenue Million Forecast, by Type of Security 2019 & 2032
- Table 17: APAC IoT Security Industry Revenue Million Forecast, by Solutions 2019 & 2032
- Table 18: APAC IoT Security Industry Revenue Million Forecast, by Applications 2019 & 2032
- Table 19: APAC IoT Security Industry Revenue Million Forecast, by End-User Verticals 2019 & 2032
- Table 20: APAC IoT Security Industry Revenue Million Forecast, by Geography 2019 & 2032
- Table 21: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 22: APAC IoT Security Industry Revenue Million Forecast, by Type of Security 2019 & 2032
- Table 23: APAC IoT Security Industry Revenue Million Forecast, by Solutions 2019 & 2032
- Table 24: APAC IoT Security Industry Revenue Million Forecast, by Applications 2019 & 2032
- Table 25: APAC IoT Security Industry Revenue Million Forecast, by End-User Verticals 2019 & 2032
- Table 26: APAC IoT Security Industry Revenue Million Forecast, by Geography 2019 & 2032
- Table 27: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 28: APAC IoT Security Industry Revenue Million Forecast, by Type of Security 2019 & 2032
- Table 29: APAC IoT Security Industry Revenue Million Forecast, by Solutions 2019 & 2032
- Table 30: APAC IoT Security Industry Revenue Million Forecast, by Applications 2019 & 2032
- Table 31: APAC IoT Security Industry Revenue Million Forecast, by End-User Verticals 2019 & 2032
- Table 32: APAC IoT Security Industry Revenue Million Forecast, by Geography 2019 & 2032
- Table 33: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
- Table 34: APAC IoT Security Industry Revenue Million Forecast, by Type of Security 2019 & 2032
- Table 35: APAC IoT Security Industry Revenue Million Forecast, by Solutions 2019 & 2032
- Table 36: APAC IoT Security Industry Revenue Million Forecast, by Applications 2019 & 2032
- Table 37: APAC IoT Security Industry Revenue Million Forecast, by End-User Verticals 2019 & 2032
- Table 38: APAC IoT Security Industry Revenue Million Forecast, by Geography 2019 & 2032
- Table 39: APAC IoT Security Industry Revenue Million Forecast, by Country 2019 & 2032
Frequently Asked Questions
1. What is the projected Compound Annual Growth Rate (CAGR) of the APAC IoT Security Industry?
The projected CAGR is approximately 38.67%.
2. Which companies are prominent players in the APAC IoT Security Industry?
Key companies in the market include Wurldtech Security Technologies Inc, FireEye Inc, IBM Corporation, Trend Micro Inc, Infineon Technologies, Gemalto NV*List Not Exhaustive, Symantec Corporation (NortonLifeLock Inc), ARM Holdings PLC, Sophos Group PLC, Intel Corporation.
3. What are the main segments of the APAC IoT Security Industry?
The market segments include Type of Security, Solutions, Applications, End-User Verticals, Geography.
4. Can you provide details about the market size?
The market size is estimated to be USD XX Million as of 2022.
5. What are some drivers contributing to market growth?
Increasing Number of Data Breaches; Emergence of Smart Cities.
6. What are the notable trends driving market growth?
Emergence of Smart City and Smart Home Developments to Drive the Market Growth.
7. Are there any restraints impacting market growth?
Growing Complexity among Devices. coupled with the Lack of Ubiquitous Legislation.
8. Can you provide examples of recent developments in the market?
August 2022 : Truvisor announced its partnership with One Identity, a unified identity security provider. The partnership would allow Truvisor to deliver One Identity solutions through their resellers' channels in Singapore, the Philippines, and Indonesia.
9. What pricing options are available for accessing the report?
Pricing options include single-user, multi-user, and enterprise licenses priced at USD 4750, USD 4950, and USD 6800 respectively.
10. Is the market size provided in terms of value or volume?
The market size is provided in terms of value, measured in Million.
11. Are there any specific market keywords associated with the report?
Yes, the market keyword associated with the report is "APAC IoT Security Industry," which aids in identifying and referencing the specific market segment covered.
12. How do I determine which pricing option suits my needs best?
The pricing options vary based on user requirements and access needs. Individual users may opt for single-user licenses, while businesses requiring broader access may choose multi-user or enterprise licenses for cost-effective access to the report.
13. Are there any additional resources or data provided in the APAC IoT Security Industry report?
While the report offers comprehensive insights, it's advisable to review the specific contents or supplementary materials provided to ascertain if additional resources or data are available.
14. How can I stay updated on further developments or reports in the APAC IoT Security Industry?
To stay informed about further developments, trends, and reports in the APAC IoT Security Industry, consider subscribing to industry newsletters, following relevant companies and organizations, or regularly checking reputable industry news sources and publications.
Methodology
Step 1 - Identification of Relevant Samples Size from Population Database


Step 2 - Approaches for Defining Global Market Size (Value, Volume* & Price*)

Note*: In applicable scenarios
Step 3 - Data Sources
Primary Research
- Web Analytics
- Survey Reports
- Research Institute
- Latest Research Reports
- Opinion Leaders
Secondary Research
- Annual Reports
- White Paper
- Latest Press Release
- Industry Association
- Paid Database
- Investor Presentations

Step 4 - Data Triangulation
Involves using different sources of information in order to increase the validity of a study
These sources are likely to be stakeholders in a program - participants, other researchers, program staff, other community members, and so on.
Then we put all data in single framework & apply various statistical tools to find out the dynamic on the market.
During the analysis stage, feedback from the stakeholder groups would be compared to determine areas of agreement as well as areas of divergence



